I need some help with a mathematical problem. A geometry problem to be specific.
Congratulations on reading this far. One of the features of Perfect Table Plan is the drawing of tables and seats on scale floor plans. The user can optionally specify how many seats and let the software calculate a sensible table size so that all the seats touch the table and their neighbouring seats. This saves the user time and produces tidy looking floor plans. Calculating the table size is trivial for square or rectangular tables. It is a bit more complicated for circular tables. But, after a bit of head scratching, I managed to work it out. Placing the seats around the circle is then trivial.
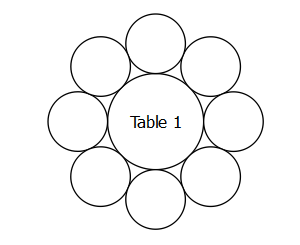
But my customers keep asking for oval (elliptical) tables, with that callous disregard customers have for how difficult a problem might be [1]. Here is the problem.
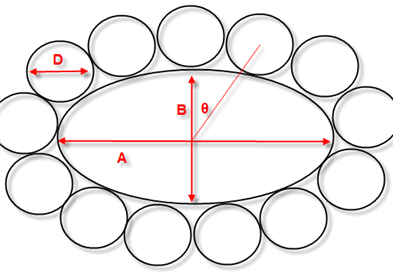
We have an ellipse E with axes A and B surrounded by N identical circles of diameter D. Each circle touches the ellipse and each of its 2 neighbours at one point, as shown above. Given N, D and the ratio A/B what is A? Given A, what is the angle THETA subtended by the centre of each circle to the centre of E?
I doubt there is an exact analytic solution to this problem. I have some vague ideas about how to tackle it. I can work out the approximate circumference C’ of an ellipse E’ that passes through the centre of all the seats (axes A+D and B+D) using the formula derived by Indian mathematical prodigy Ramunajan.
From this we should be able to work back to A. As N becomes large C’ will tend to N*D. For smaller N, C’ will diverge from N*D so we might have to use an iterative method[2] to calculate A, but we can use the approach above to get a starting value for A and then iterate numerically from there.
I am less sure about how to work out the angle THETA for each circle. But if we pre-compute the angles of, say, 100 equally spaced points around E we could use these to interpolate the position of N circles where N is <= 100. It might be OK to place the first circle at THETA=0 for all values of N>0, I’m not sure.
Several hours on Google didn’t turn up a solution. Surely I am not the only person to have tackled this problem in human history? Can anyone point me at a workable solution? Preferably with code.
Alternatively can somebody write me the code to solve the problem? Maybe there is someone out there with a mathematical background that would relish the challenge? I am prepared to pay for working code that I can use in PerfectTablePlan (a few hundred dollars, negotiable).
- To simplify things we can assume a fixed value of A/B, say 1.5 .
- It needs to work for N from 1 to 99.
- The solution doesn’t need to be exact, but it has to look OK to the human eye. No overlaps and no big gaps.
- Low values of N might need to set up as special cases. E.g. it isn’t possible to get all the circles to touch if N <=6 (and possibly higher values of N depending on A/B).
- The solution must be returned in a reasonable time, ideally under 0.001 seconds and definitely less than 0.01 seconds. It can store pre-computed values, e.g. in an array. But it mustn’t require excessive memory.
- The code needs to be in a form I can easily convert to C++. C, Java, BASIC or Python should be fine. Haskell not so much.
- Ideally it should come with a simple GUI that allows me to set the value of N and D and see the result visually.
If you want to be paid I need to be able to buy all rights to the code and it mustn’t be released into the public domain (i.e. don’t post the code on this blog). In the unlikely event I get more than one set of working code, I will pay for the best solution according to the above criteria. Contact me for more details.
[1] I love them all really.
[2] For example Newton-Rhapson.
**** UPDATE ****
See https://successfulsoftware.net/2008/08/25/a-mathematical-digression-revisited/ .

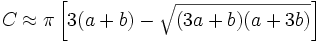
 I loved Lego as a child. Now I have a two year old son I have a good excuse to play with it all over again. Below are some of things I have managed to construct out of Lego Duplo with his ‘help’ (building something out of Lego with a two year old reminds me of playing Tetris, only in 3 dimensions rather than 2).
I loved Lego as a child. Now I have a two year old son I have a good excuse to play with it all over again. Below are some of things I have managed to construct out of Lego Duplo with his ‘help’ (building something out of Lego with a two year old reminds me of playing Tetris, only in 3 dimensions rather than 2).











 A couple of weeks ago I received a rather expensive looking tie in the post. I hadn’t ordered it and there was no note or letter to say who it had come from. How very odd. As a
A couple of weeks ago I received a rather expensive looking tie in the post. I hadn’t ordered it and there was no note or letter to say who it had come from. How very odd. As a 
 In the 10 months that I have been writing this blog I have pointed the finger at quite a few companies I consider to be giving less than great service. I would like to even that up a bit by recommending
In the 10 months that I have been writing this blog I have pointed the finger at quite a few companies I consider to be giving less than great service. I would like to even that up a bit by recommending  Ripoff: A ripoff (or rip-off) is a bad deal. Usually it refers to an incident in which a person pays too much for something. A ripoff is distinguished from a
Ripoff: A ripoff (or rip-off) is a bad deal. Usually it refers to an incident in which a person pays too much for something. A ripoff is distinguished from a  Fraud can be a very big problem for online software vendors. Fraudsters can easily use throwaway email addresses that can’t be traced back to them (e.g. Hotmail) and IP addresses aren’t difficult to hide. Not only does the vendor lose the payment when the fraud is reported, they also often get hit with a chargeback fee. This is pretty outrageous when you think about it – the credit card companies are charging vendors for the fraudulent transactions that they themselves have failed to detect.
Fraud can be a very big problem for online software vendors. Fraudsters can easily use throwaway email addresses that can’t be traced back to them (e.g. Hotmail) and IP addresses aren’t difficult to hide. Not only does the vendor lose the payment when the fraud is reported, they also often get hit with a chargeback fee. This is pretty outrageous when you think about it – the credit card companies are charging vendors for the fraudulent transactions that they themselves have failed to detect. There are a few certainties in life: death, taxes and harddisk failure. I have no less than 6 failed harddisks sitting here on my desk patiently awaiting their appointment with Mr Lump Hammer. 2 Seagates, 3 Maxtors and 1 Western Digital. This equates to roughly one disk failure per year. Perhaps this is not suprising given that I have about 9 working harddisks at the moment spread across various machines. Given the incredible tolerances to which harddisks are manfactured, perhaps it is a miracle harddisks work at all.
There are a few certainties in life: death, taxes and harddisk failure. I have no less than 6 failed harddisks sitting here on my desk patiently awaiting their appointment with Mr Lump Hammer. 2 Seagates, 3 Maxtors and 1 Western Digital. This equates to roughly one disk failure per year. Perhaps this is not suprising given that I have about 9 working harddisks at the moment spread across various machines. Given the incredible tolerances to which harddisks are manfactured, perhaps it is a miracle harddisks work at all.